Certified Red Team Professional (CRTP) Review

\x01 Introduction
Hey, I didn't wait months after clearing the exam to write a review for it, unlike my PNPT review! I recently sat the Certified Red Team Professional exam and wanted to give my honest feedback and opinions on the course along with the exam.
I took the CRTP course right on the heels of clearing the PNPT exam (you can read that review here) and was excited to put Kali to the side and attack Active Directory using nothing but PowerShell. With a lot of courses built around Kali and attacking with Kali, it was pleasant to do everything from Windows for a change. It wasn't without growing pains, but I enjoyed using PowerShell more in-depth nevertheless.
Okay, so what is the course all about and what are you going to learn? According to Pentester Academy, you will learn -
- Practice various attacks in a fully patched realistic Windows environment with Server 2016 and SQL Server 2017 machines.
- Multiple domains and forests to understand and practice cross-trust attacks.
- Learn and understand concepts of well-known Windows and Active Directory attacks.
- Learn to use Windows as an attack platform and use trusted features of the OS like PowerShell and others for attacks.
- Try scripts, tools, and new attacks in a fully functional AD environment.
As far as prerequisites, all you need is a basic understanding of Active Directory with some knowledge of the Windows command line interface. Nikhil Mittal does an outstanding job at stepping you through the entire attack chain starting from an assumed breached scenario. He will walk you through topics such as
- Domain enumeration
- Local privilege escalation
- Domain enumeration
- Lateral movement
- Domain persistence
- Domain privilege escalation
- Cross forest attacks
- Forest persistence
Without further ado - let's kick this off with the purchase options ⬇️
\x02 Purchase Options
There are three options to select from for the length of lab time: 30 days, 60 days, and 90 days. When I reserved my time, they had discounts on the pricing due to COVID-19.
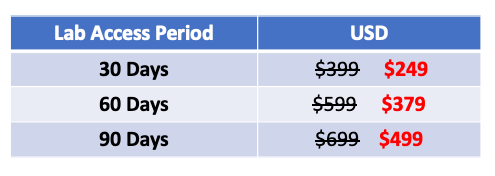
I went with 90-days of lab access and did so to buy myself time as I didn't want to rush through things when I didn't need to. Looking back, I didn't need 90-days coming off the heels of the PNPT as there was overlap in content, but there were still things I learned that I am glad I had spare time to test in the lab environment – looking at you, constrained delegation.
After you purchase the lab time, you have 90 days from the date of purchase to begin your lab time. You get 14 hours of video content to go through and one exam attempt. Each additional exam attempt is $99 if you need it.
If you are interested in booking your CRTP lab seat, head over to the Active Directory Lab page and click on "Purchase Options" to get started.
\x03 My Thoughts on the Course
Overall, I loved the course. Admittedly, there was some content overlap between the PNPT and CRTP, but that wasn't a big deal because even though the content was similar, using PowerShell for everything added a twist.
When you purchase the lab, you get 14 hours of pre-recorded videos to work through with a course lab guide to follow. What I really liked about the course, and the lab was the fact it's more of a walkthrough in a way. You aren't dropped in a massive environment and told to "figure it out". There is no head-banging here.
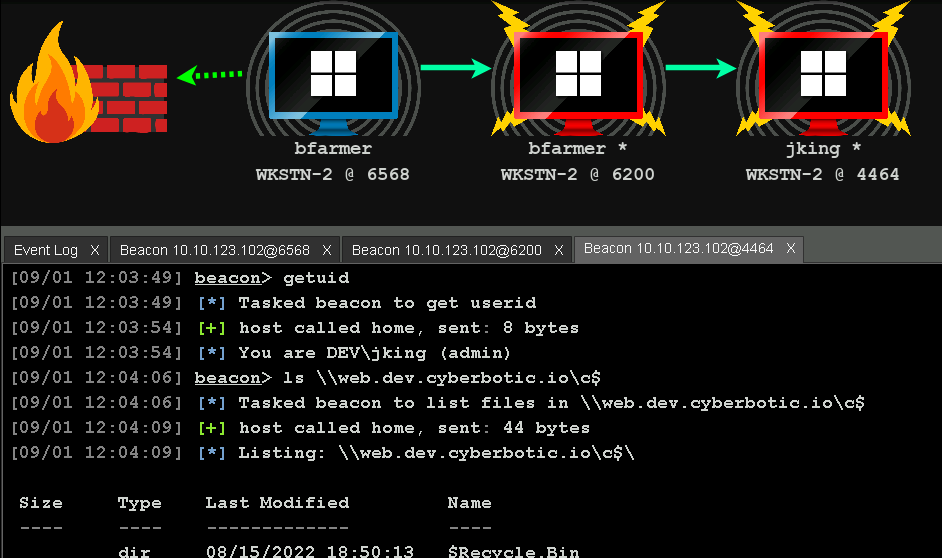
Instead, Nikhil will show you something, say using PowerView to enumerate domain trusts, and you are given the chance to replicate the same thing in the lab environment. I enjoyed this approach. The idea here is you watch the video, take good notes, and then try your hand at what you just watched. By the time you complete the course videos, you worked your way through the entire attack lifecycle starting from initial domain enumeration to AD forest persistence.
As you work through the course, there are flags for you to capture that are then put in a portal and you're told if it's correct or not. Flags can be things like a SID, ACL rights, and other domain artifacts. While this was a nice addition, there are two things I didn't really like about the flag submission process -
- The process to get the flag follows the course 100%. What I mean by this is you can answer the question without even doing it yourself because more often than not, the answer to the question is covered directly in the course material.
Some of the prompts were worded a bit odd which made it difficult to understand what was being asked of you. I would get the answer but sometimes it wasn't accepted. Overall, these small things didn't distract from the learning and didn't mind them too much.
Extra Comments
Throughout the entire course, and exam, you focus solely on Active Directory misconfigurations to further your attack strategy. There are no patchable exploits you can leverage so forget about using exploits or anything off Exploit-DB. None of that here. You need to really understand AD and complete your enumeration to be successful in the course and exam.
The one thing I would point out is the fact that while BloodHound is covered, it's done so very lightly. I would suggest you look into BloodHound more in-depth to understand what the edges mean to understand an attack path. Also, make sure you get the correct version of SharpHound to match the version of BloodHound you're running or you will waste time trying to correct it.
\x04 The Exam Experience
After working through all of the course material, I felt prepared to take the exam. Starting the exam is as simple as pressing a button in the student portal and waiting about 15 minutes while your exam environment is built. I liked the fact you can start the exam whenever you wanted and without any proctoring. Once started, you get 25 hours to attempt to complete the exam objectives. You get 25 hours rather than 24 hours to make up for the time it takes to spin up the environment.
I was sitting around one Friday afternoon and debated just starting it right then and there. After many "are you sure?" prompts in the student portal, my exam attempt started 15 minutes later. It was go time - no going back now.
Exam Overview
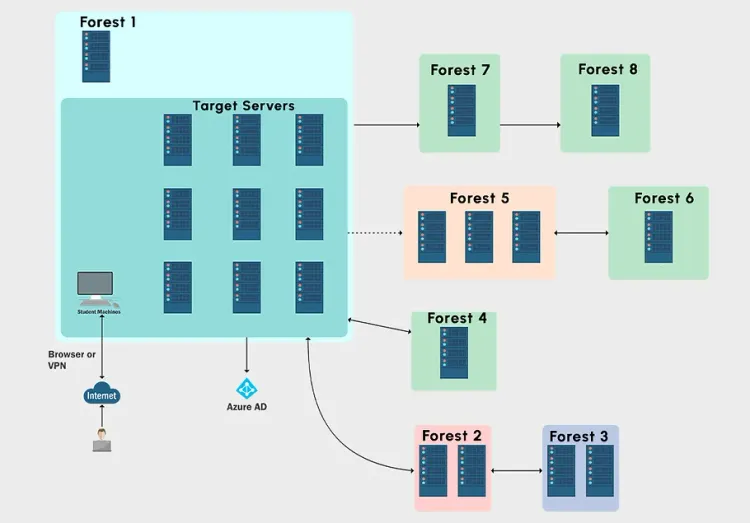
The exam environment contains a total of 5 target machines spread over different domains that you need to get code execution on, albeit doesn't have to be privileged access. Overall, the exam was great. There were a few twists that were added to the environment that made it a joy to work through. Don't think you can just copy/paste commands from the course and expect them to work on the exam.
One thing to note - unlike in the lab environment, the student machine in the exam does not have any tools installed. You are responsible for uploading the tools you need/want to the VM to use during the exam. Just wanted to throw that out there.
Starting the Exam
I started my exam at 1415 and ended up getting privileged access on the first machine after less than an hour. Due to my enumeration with BloodHound and PowerView, I had pretty much plotted the exact path I needed to take to own the entire domain. From the initial machine, the jump to the next host was relatively easy and after I had compromised the second host, I was feeling pretty good...but not for long.
I missed something
As I said, I knew the path I needed to follow to own the domain - but I couldn't figure out the jump between the second machine and the third machine. I was missing something during my post-exploitation enumeration on the second machine that was stopping me. I just knew it. Around this time, I am a few hours in and ended up taking a break for dinner. Once back at my desk, I ended up going through some of my notes and had an epiphany! I had missed something during my enumeration on the second host. I ended up finding exactly what I needed from that host to allow me to move laterally to the third host and then on to compromise the entire domain.
I am kicking myself to this day because I knew each step in the path, but that one thing held up my progress. ONE THING.
Checkmate
After about 8 hours in the exam environment, I had reached the goal! I had privileged access on every single machine in the environment and felt great about where I stood. I went back through my notes to make sure I had everything I needed before starting my report. In the excitement, I missed a few important screenshots (don't do this, please) so I had to go back and get those. All in all, I went to bed around 2 am feeling pretty good and ready to start the report a few hours later.
\x05 Reporting
Having just completed my PNPT report, I wanted to do something different with the report for the CRTP. I wanted to get away from transferring notes from one platform to a Word template and checking to make sure the images were aligned and small details like captions and references to past findings were dialed in.
Report Ranger ❤️
Enter Report Ranger by the brilliant team at Volkis. I took the time to follow the installation guide and customized my report before my exam attempt and I am so glad I did. Using Report Ranger was an absolute lifesaver when it came to generating the report and dealing with the small details. All I needed to do was create a new markdown file for each finding along with adding supporting information (descriptions, evidence, mitigations, etc.) and Report Ranger did the rest. It takes care of adding captions to images, finding numbering, and finding order for you. It was great to use and yielded a great-looking report.
If you want to learn more about Report Ranger, I would direct you to the playlist on the Volkis YouTube channel. I even had a small chat with an individual that works at Volkis and shared my thoughts and praise about Report Ranger and learned a few things along the way. I know 100% that I am using Report Ranger from here on out.
My report was 36 pages long and had descriptions, business impact, exploitation walkthroughs, remediation steps, and references for each of the findings.

Report Timeline
I turned in my report on the 24th of September and received an email on the 25th confirming the lab support team received my report and that I would know the result within 7 business days.
On the 29th, I received another email that I passed and that my certificate from Accredible would be issued within a week (I received it the same day!).
\x06 Overall Thoughts
Overall, I really enjoyed the course and enjoyed the exam even more. It was a breath of fresh air getting away from Kali Linux and using nothing but offensive PowerShell to complete my attacks. PowerShell brought with it a few quirks as I wasn't as familiar with it, but after this, I like it. I am already planning on taking the CRTE after the CRTO!
If you want to learn more about Active Directory exploitation and want a practical, hands-on exam, this is your ticket. I thought this paired very well with the PNPT course and also is a good gateway to the CRTE.